Command policies are the first type of policies we see. Their expression define, what users are allowed to do.
Command policies are regular expressions (RegEx) to command-line commands. ^show for example, will allow everything, starting with ‘show’. Don’t be scared if you don’t know about RegEx, there is also a wizard to create command policies.
The build-in policies:
There are five built-in command policies for normal use and four for use with partitions. Partitions will be mentioned later, so let’s have a look at the normal ones.
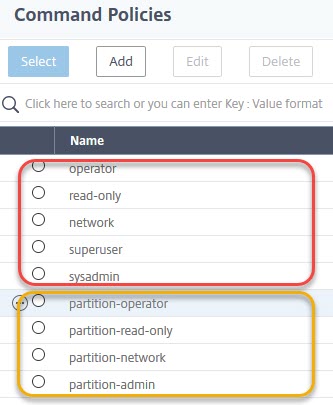
Policies for normal use (red) and for partitions (yellow)
- read-only:
(^man.*)|(^show\s+(?!system)(?!configstatus)(?!ns ns\.conf)(?!ns savedconfig)(?!ns runningConfig)(?!gslb runningConfig)(?!audit messages)(?!techsupport).*)|(^stat.*) - operator:
(^man.*)|(^show\s+(?!system)(?!configstatus)(?!ns ns\.conf)(?!ns savedconfig)(?!ns runningConfig)(?!gslb runningConfig)(?!audit messages)(?!techsupport).*)|(^stat.*)|(^(enable|disable) (server|service).*) - network:
^(?!clear ns config.*)(?!scp.*)(?!set ssl fips)(?!reset ssl fips)(?!diff ns config)(?!shell)(?!reboot)(?!batch)(?!source)(?!install)(?!set\s+aaa\s+parameter\s+.*-maxLoginAttempts.*)(?!lock\s+aaa\s+user\s+.*)(?!unlock\s+aaa\s+user\s+.*)(?!(set|unset|add|rm|bind|unbind|switch)\s+ns\s+partition)\S+\s+(?!system)(?!audit messages)(?!configstatus)(?!ns ns\.conf)(?!ns savedconfig)(?!ns runningConfig)(?!gslb runningConfig)(?!techsupport)(?!nstrace).*|(^install\s*(wi|wf)) - sysadmin:
^(?!shell)(?!sftp)(?!scp)(?!batch)(?!source)(?!.*superuser)(?!.*nsroot)(?!install)(?!show\s+system\s+(user|cmdPolicy|file))(?!(set|add|rm|create|export|kill)\s+system)(?!(unbind|bind)\s+system\s+(user|group))(?!diff\s+ns\s+config)(?!(set|unset|add|rm|bind|unbind|switch)\s+ns\s+partition).*|(^install\s*(wi|wf)) - superuser:
.*
Your own policies
Why should I create command-policies?
There is no real ‘need’, but customers usually ask for users, being limited to – let’s say – gateway. So it’s your duty to create policies allowing access to gateway only. Let’s try to create a policy for that.
System → User Administration → Command Policies
Click add.
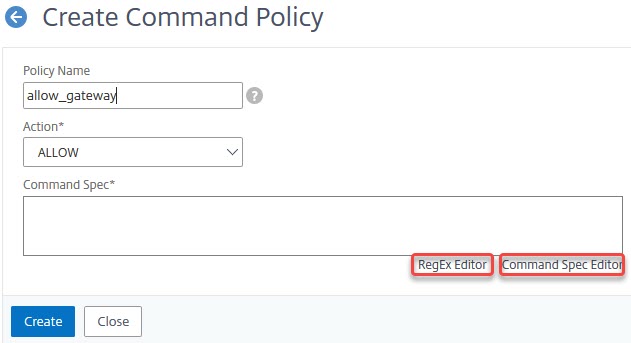
You may type your commands into this Command Spec* field, if you are very familiar to both, RegEx and NetScaler syntax, or use one of the two built-in editors.
The RegEx Editor
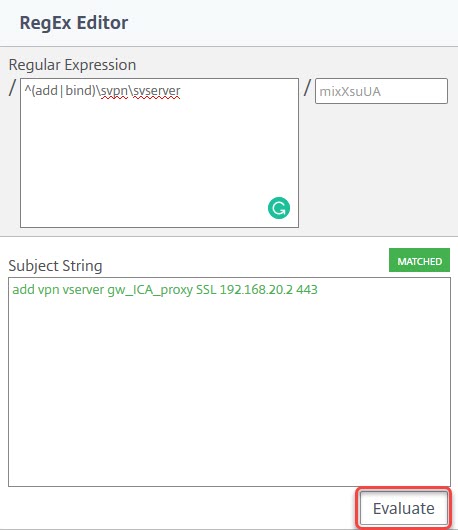
^(add|bind)\svpn\svserver
^ starts with
() is a group, containing add and bind
\s is a white-space (space, tab, line break)
Paste the original command into the edit box called “Subject String”. Then try to create a RegEx matching it. In this case, we have add vpn vserver, but there is also bind vpn vserver. In this case, it does not make sense to specify more than add or bind vpn vserver, as this would allow changes to all gateway servers. However, it would not allow deleting these gateway servers. If you want to allow this in addition, you would have to change the first part to ^(add|bind|rm) (add or bind or rm).
Different to what Citrix says, NetScaler OS is using python RegEx, not PCRE!
We would need some more policies, as we would also need to be able to create and modify session policies (add vpn sessionPolicy), probably authorization policies, intranet applications and many more.
The command spec editor
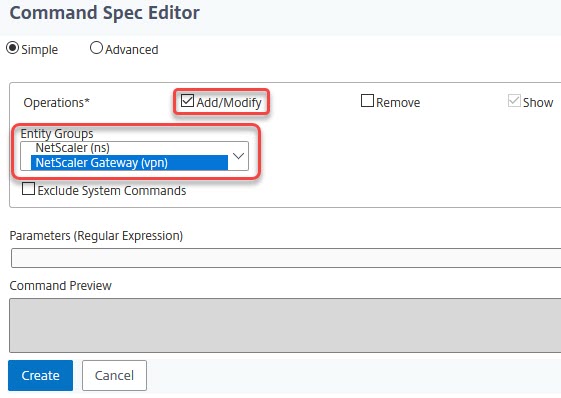
Unfortunately, the drop-down box for ‘Entity Groups’ does not work well with most versions of Citrix ADC / NetScaler firmware, so it’s a little bit tricky to use.
Find the object you are interested in, tick the checkbox for Add/Modify and or Remove. You may select more than just one object at the same time. The result will always be a RegEx. In this case: (^(?!rm)\S+\s+vpn\s+\S+)|(^(?!rm)\S+\s+vpn\s+\S+\s+.*).
[wpedon id=”798″ align=”center”]
