Our load-balancing vServer allows authenticated traffic. But is a single factor enough? During our project work, we see a strong move to use more than just one factor to authenticate to rise security.
We want to see a second factor to mee security requirements. To keep things simple we use local authentication as a second factor.
 Requirements: This lab requires the authentication lab.
Requirements: This lab requires the authentication lab.
Creating a local AAA user
We need to create a local user with the same user-name as the domain user, but a different password. My domain user is johannes.norz, so I will create a local AAA user on this Citrix ADC/NetScaler, the password will be 1234.
Navigate to Security → AAA-Application Traffic → Users. Click Add.
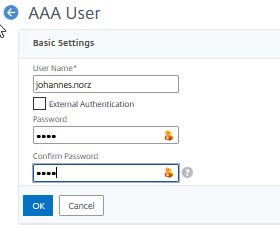
Give this user a name, uncheck External Authentication and specify a password. That’s all.
Creating a multifactor autrhentication structure
The logon dialogue for the second factor
Every factor needs a logon dialogue. There is a designer built into Citrix ADC.
Navigate to Security → AAA-Application Traffic → Login Schema. Click Add.
Give your schema a name. Add a Profile by clicking add.
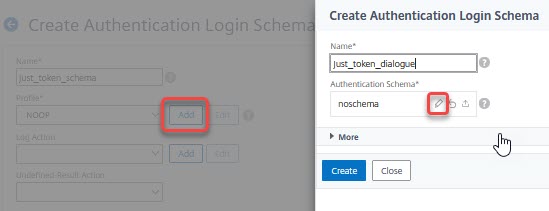
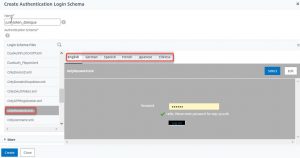
Give this profile a name and click the little pencil. A folder containing built-in schemas will pop up. Click the folder to see the schemas.
Select the schema OnlyPassword.xml. You may change the layout, add text and change labels for all languages supported by clicking Edit.
After finishing click select and create.
Now type true to the policy rule and click create to close the create authentication login schema policy dialogue.
Congratulations, you just created your first logon dialogue!
The policy label
Factors in n-factor authentication always consist of a policy label, containing one or more logon policies and the login schema policy. Every factor is a policy label on its own.
Navigate to Security → AAA-Application Traffic → Authentication → Advanced Policies → Policy Label. Click Add.
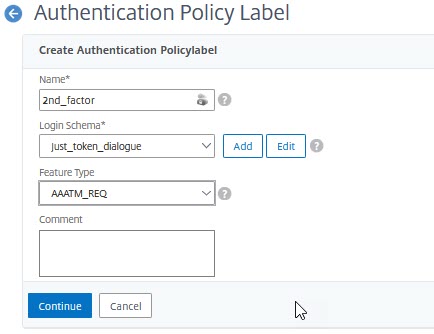
Give this label a name, select the login dialogue profile, created in the step before and click continue.
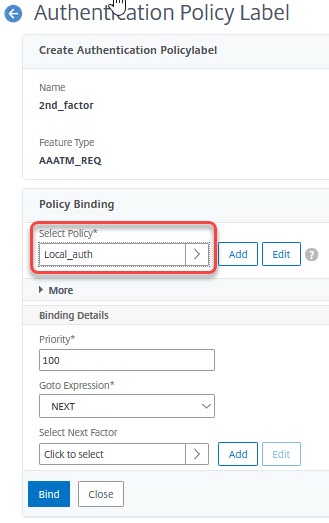
Bind the local authentication policy created during the previous lab into this label. Click Done.
Invoking this policy label
Every factor has to be invoked by the previous factor. That’s true for our “new” factor as well.
Open the AAA vServer ( Security → AAA-Application Traffic → Virtual Servers).
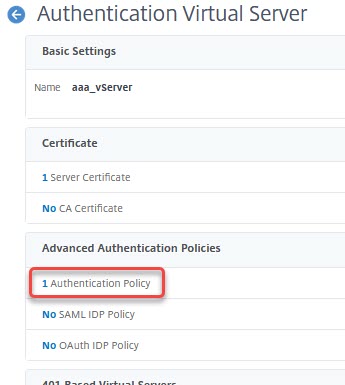
Open the authentication policy binding.
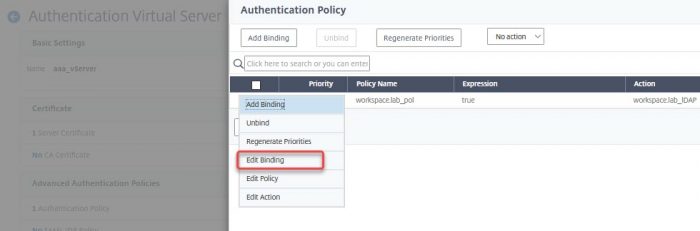
Click edit binding (or select the policy and select edit binding from the action drop-down box)
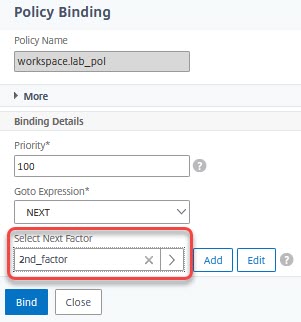
Click select next factor and select the policy label created during the step before. Click Bind.
Testing
Surf to your load-balancing vServer. You should see a logon dialogue like before, but a second dialogue after logging on successfully. The password is the password of your local user. Logon should be possible like before but this time using a second factor.
[wpedon id=”798″ align=”center”]